Cyber Security is the combination of acceptable measures for security in the use of the Internet and digital technologies. Cyber Security aims to ensure the protection of confidential information and data of Internet users. This is very important for various organizations and those who work online and store confidential information. In more detail, using cyber security can essentially block a system and take a strong stance against hackers and other cyber intruders.
Who are the victims of cyber-attacks?
Companies or organizations, which have a lot of important information, and customer data, especially news media, banks, and e-commerce companies are most susceptible to cyber-attacks. Also, if a person's social media account is hacked, it becomes a cyber attack. Hackers mainly target popular people for cyber attacks on social media accounts.
Types of Cyber Attacks:
1. Phishing: Phishing is a cyber attack process, which provides false information about users online and tries to steal site links, IDs, or passwords used by users. Phishing attacks usually occur via email or messaging. Hackers send people a fake email or message and the email or message contains links to click on. This link takes the user to a fake website that gives opaque feedback. Through this website, hackers steal the information of many gurus including the user ID, and password. The purpose of this attack is to steal information used by users and use it to attack others.
2. Malware: A malware cyber attack is a type of computer attack where hackers attach malware to a computer or network to gain control over a system. Malware cyber attacks can cause numerous damage to computers, such as stealing personal information, installing malware on other computers on the network, and sending spam or phishing emails using these tools.
3. Ransomware: Ransomware is software that provides detailed information about your computer's memory resources. Hackers can collect information about your computer's memory using ransomware through any software or anti-virus.
Ransomware hackers can use your computer's memory to access your browser and monitor your network traffic. Hackers can run search engines or other programs on your computer and gain control of your entire computer.
Example: Suppose you go shopping with every door in your house locked and keyed. You come and find that someone has broken the locks of all the doors in your house and locked all the doors with some of your own locks. And they are demanding to get the key to that lock by giving them money, only then you can open the lock and enter the house. It seems strange, doesn't it? Yes, ransomware is one such malware virus.
4. Denial of Service (DOS): Denial of Service (DOS) is the dreaded name for business. In this type of attack, the number of traffic on certain organizations' systems, servers, and networks increases which disrupts the service. Websites slow down or shut down due to high server traffic. It is also known as Distributed Denial of Service (DDOS).
5. Insider threat: This type of attack is carried out by someone inside the organization. Especially those who have control over networks, servers, and domains conduct these attacks. Basically, it is caused by greed, hatred, and even carelessness in small business enterprises.
6. Zero Day Exploit: This attack is more common after announcing that there might be a problem with the network. Given the problem, service providers and developers work on solutions within a certain period of time. At this time, the attackers attacked. They gather information before solving problems.
Cybercrime & cybersecurity statistics:
According to Microsoft, nearly 80% of nation-state attackers targeted government agencies, think tanks, and other non-government organizations. Microsoft also reports that 58% of cyberattacks from nation-states were in Russia.
Cyber security statistics indicate that there are 2200 cyber attacks per day, with a cyber attack happening every 39 seconds on average. Global cyberattacks increased by 38% in 2022, compared to 2021. 83% of organizations had more than one data breach in 2022. 82% of all breaches involved 'the human element' (the use of stolen credentials, phishing, misuse, or human error) in 2022. It is estimated that an estimated 33 billion accounts will experience a breach in 2023.
The main goal of cyber attackers is to collect information (eg: names, passwords, and financial records); Which is then sold on the dark web.
Cyber attack in Bangladesh:
On February 4, 2016, 81 million dollars or approximately 640 crore Taka (Six hundred and forty crore Taka) was stolen from the account of Bangladesh's central bank 'Bangladesh Bank' through digital hacking, which was deposited in the United States Federal Reserve Bank of New York. (1$ = 79 Tk approx; Date: 04 February 2016)
To stay safe from cyber attacks:
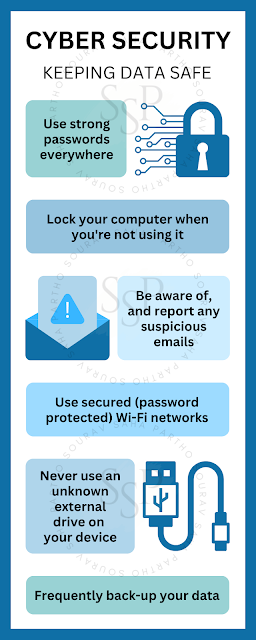
1. Keep your software updated regularly.
2. Use antivirus protection and firewalls.
3. Use strong passwords and password management tools. Never share your account password or verification code with anyone. Not even with your own family members or friends.
4. Use two-factor authentication or multifactor authentication such as Google, or Microsoft Authenticator.
5. Be aware of phishing scams – be very suspicious of emails, phone calls, and flyers, and avoid sharing phishing links with friends and family members.
6. Be aware of the sharing of your personal information (eg: name, email, phone number, birth date, IP address, social security number, location details, physical or digital identity data, and your credit/debit card information).
7. Use all kinds of devices carefully, including your phone, and computer.
8. Back up your data frequently.
9. Don't use public Wi-Fi.
10. Review your online account and credit report regularly for changes.
11. Before providing your personal information (eg name, phone number, location, email address, etc.) to any website, identify them properly.
Conclusion: All information and data used in this blog are collected from Google, websites, TV or magazine reports, and various research papers and it is not my intention to denigrate any person or organization. This blog is written for awareness raising purposes only. This blog has been translated into English with the help of 'Google Translate'. Thank you.